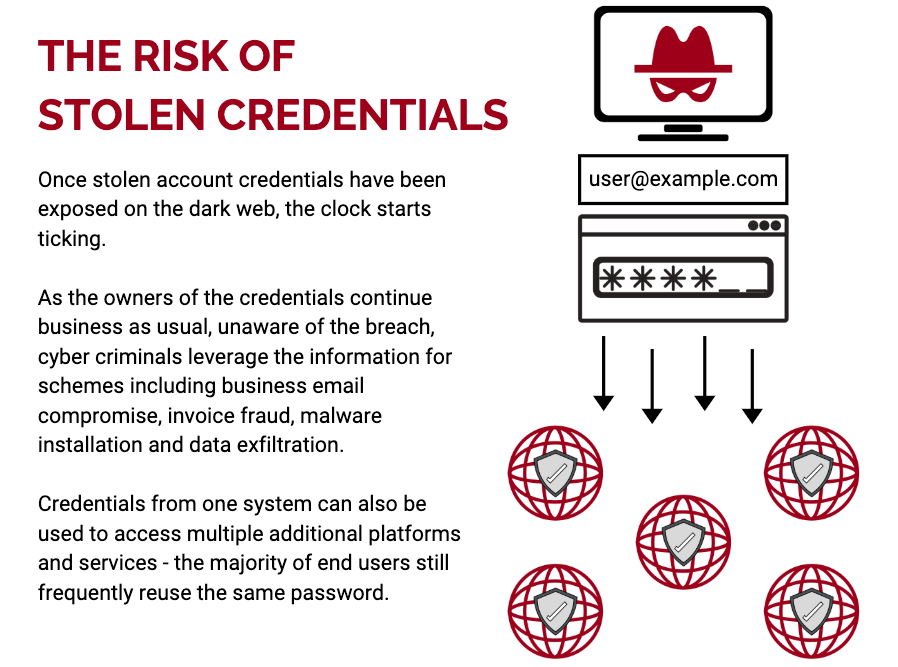
For cybercriminals looking to steal access credentials, there’s never been more options. Whether it’s using social engineering to trick a user into handing over details, or delivering malware via an email, we are all vulnerable to having our networks breached.
This growing trend has led to vast volumes of stolen credentials available for sale across the dark web. Some reporting from earlier this year estimated at least 773 million breached email addresses were available in a single cache for sale. Once those details are exposed, a huge range of individuals have access to it from professional fraudsters to bored hacktivists. You don’t just have to worry about fraud and theft - professional liability and reputational damage are also increasingly a concern.
Unfortunately, despite years of being warned not to reuse passwords across multiple platforms and services, this sage advice is still ignored by the majority of end users. Rampant password reuse significantly escalates the impact of credentials theft, as cybercriminals use one set of breached login details across multiple platforms and services.
Ultimately there is no guaranteed way for users to avoid credentials theft and keep personal data off the dark web; cybercriminals create new methodologies every day. So how do you mitigate the business impact of credentials theft for your employees and clients?
How should organisations respond to this threat?
With such a large-scale challenge, it’s vital for organisations to take a proactive approach to protect their clients and employees. By going beyond standard tools such as password managers and investing in dark web monitoring tools, it is now possible to mitigate the worst outcomes of credential theft. Cybercriminals often hold back their data for months before exploiting or selling their cache. In fact, compromised credentials go unreported for an average of 15 months after the breach occurs – affected companies are often only made aware when law enforcement has notified them. By consistently monitoring the dark web for breached credentials, it’s possible to identify stolen data and rotate passwords accordingly before cybercriminals can exploit your details.
Another crucial best practice is to limit the potential attack surface area wherever possible. Some of the more innovative MSPs are now introducing premium services to users’ family members to monitor the dark web for their personal account credentials. Due to password reuse, personal accounts are another frequent source of compromise that can lead to corporate networks being breached using the same credentials. By extending your monitoring to include your users’ extended network, you will have even greater visibility of any issues before the threat can escalate and impact business as usual.
Darkbeam’s dark web monitoring solutions help you to identify stolen credentials faster than ever before and neutralise them before they can be used against your organisation.
We monitor multiple dark networks including Tor, I2P, Freenet and GNUnet to search for compromised credentials and visualise the results safely in our platform so our users never have to interact directly with the dark web. Want to know more? Get in touch at info@darkbeam.com today.
