More and more organisations are choosing to adopt the MITRE ATT&CK framework to add maturity to their IT security programs. This framework helps organisations manage their cyber risk and helps professionals understand the tactics used in cyber attacks the from different hostile groups.
What is the MITRE | ATT&CK Framework?
The MITRE Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK) framework is a curated knowledge base of adversary tactics and techniques based upon actual observed patterns. The tactics and techniques within the framework form a common taxonomy that can be used to describe and model the offensive and defensive components of a cybersecurity strategy. ATT&CK is a globally recognised framework that is used as the foundation of threat models and methodologies within all parts of the public and private sectors.
The MITRE | ATT&CK FRAMEWORK
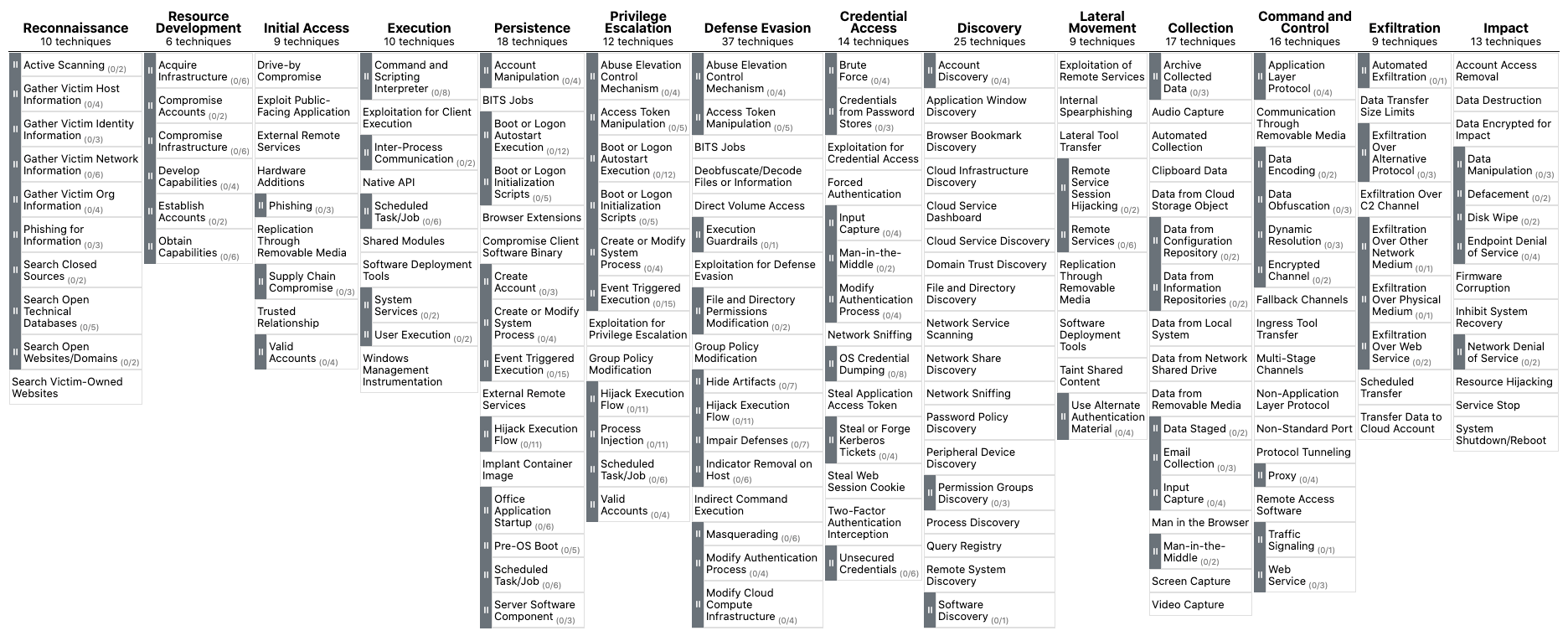
Fig 1. MITRE | ATT&CK Matrix
The ATT&CK framework is usually visualised as a matrix, with columns representing the fourteen tactics used to categorise specific objectives, and each cell within a column representing a technique. Tactics represent the “why” of an ATT&CK technique and are the adversary’s objective for performing a specific action. They also provide useful contextual categories for techniques. The tactics are:
- Reconnaissance - gathering information to plan future operations.
- Resource Development - establishing resources to support operations such as setting up a command-and-control infrastructure.
- Initial Access - trying to get into a network e.g., spear phishing.
- Execution - trying the run malicious code.
- Persistence - trying to maintain a foothold.
- Privilege Escalation - trying to gain higher-level permissions.
- Defense Evasion - trying to avoid being detected.
- Credential Access - stealing accounts names and passwords e.g., keylogging.
- Discovery - trying to identify resources within an environment.
- Lateral Movement - moving through an environment.
- Collection - gathering data of interest to support an objective.
- Command and Control - communicating with other compromised systems to control them.
- Exfiltration - stealing data.
- Impact - manipulate, interrupt, or destroy systems and data e.g., ransomware.
Techniques represent the “how”, and describe how an adversary achieves a tactical objective by performing an action. Techniques may also represent “what” an adversary is seeking to achieve by performing an action. Some techniques also have sub-techniques that provide additional detail regarding the actions of an adversary.
A typical attack sequence would involve at least one technique per tactic, and a completed attack sequence would be built by moving from the left side of the matrix to the right i.e., from Reconnaissance to Impact. It is not uncommon for multiple techniques to be used per tactic, and a sequence does not need to include every tactic. An attack will commonly use the minimum number of tactics to achieve an objective. Attack sequences can then be mapped into the ATT&CK framework and visualised:
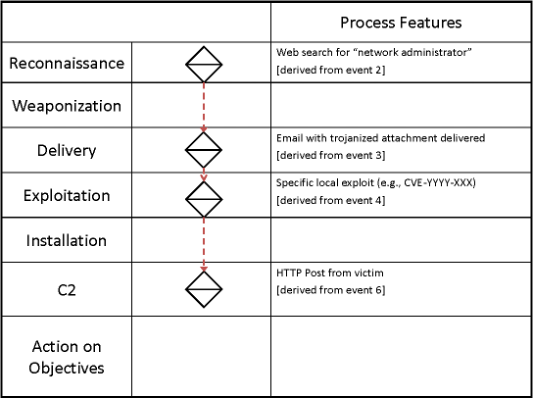
Fig 2. Example Attack Sequence
ATT&CK provides a useful high-level way of assessing the potential threats to your network, as well as the various strengths and weakness that exist within your existing defences.
Further detail can be added by looking at which Common Weakness Enumeration (CWE) categories a tactic and technique exposes you to, and then mapping those CWEs to specific Common Vulnerability and Exposures (CVE).
Why Darkbeam aligned to MITRE | ATT&CK FRAMEWORK?
Darkbeam focuses upon finding the externally available information that an adversary would use to assess the feasibility of an attack, or to assess the potential strengths or weaknesses that might exists inside your network. These techniques are usually (but not exclusively) found within the Reconnaissance column and represent the first step in a tactical advance from left to right through the matrix. By ensuring you have a very low information exposure footprint, it is less likely that an attacker will be able to progress further.
