Global law enforcement agencies took down Genesis Market, one of the largest online marketplaces for stolen passwords and sensitive data this week.
The enormous scale of the website - and its remaining competitors - serve as a stark reminder that companies' systems are under constant threat, meaning that unmitigated risks in the supply chain leave businesses continuously exposed to the implications of supplier-held data being compromised in an attack.
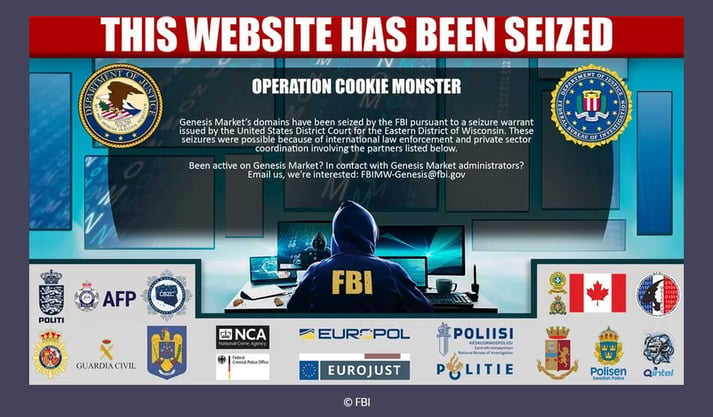
Genesis Market has been linked to cyber attacks against businesses including the game publisher Electronic Arts - which led to sensitive data including the source code of the popular FIFA games being taken.
This shutdown is not the end of the problem
Genesis Market was enormous. It sold data taken from over 1.5 million computers and 80 million online accounts. But it is not alone - Genesis Market was one of many places that 'access brokers' can sell stolen credentials.
The website was suspected of having strong links to Russia. In the ecosystem of cyber criminals, it was an example of an ‘access broker’ or ‘access shop’. These are websites (often on the dark web, although Genesis Market was available on the normal internet) which sell access to systems or user accounts which can then be used to launch ransomware or other attacks.
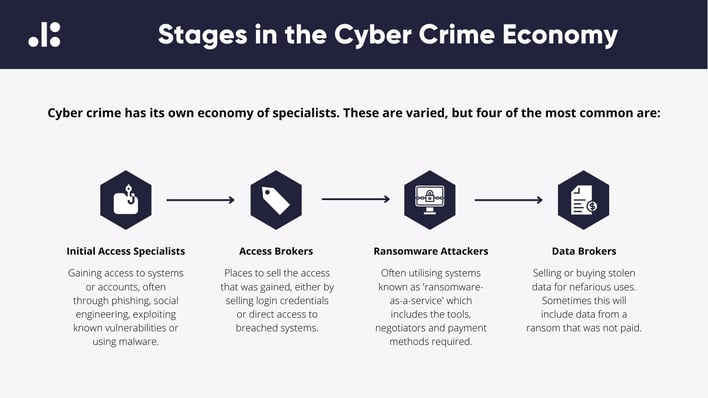
Genesis Market offered 80 million stolen accounts, including personal and work-related logins (such as email and software). This serves as a stark reminder that even if a company secures its own systems, the enormous scale of cyber crime means that all of its suppliers and third-parties are under threat - but the business often has little or no visibility over the scale of these risks.
As easy as shopping online
Genesis Market was exceptionally easy to use. It was accessible with a normal internet browser and even had an FAQ page to help new users.
A supplier or partner's breach can lead to devastating consequences such as data leaks, service disruptions, or direct attacks on the company. Government organisations (including the UK’s NCSC) are increasingly recommending that companies monitor their suppliers and other external partners for cybersecurity risks and incidents.
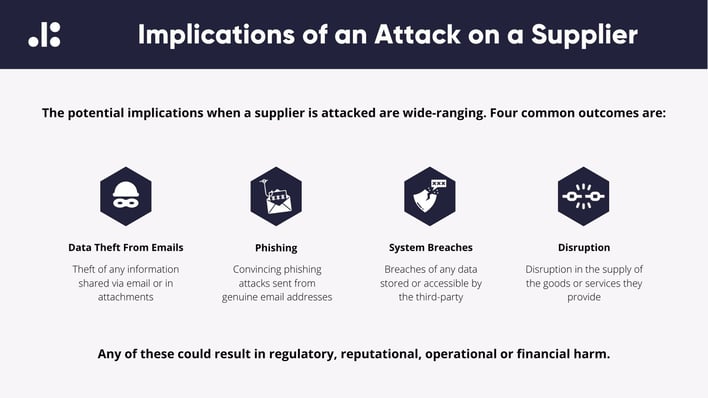
To mitigate these risks, companies should monitor their third-party relationships for cybersecurity vulnerabilities and set up alerts for breaches. However, this can be challenging due to stretched security teams and procurement teams lacking cybersecurity knowledge coupled with their own significant workloads.
Darkbeam's Supplier Cyber Risk Management platform addresses these concerns by providing instant vulnerability assessments and accessible dark web monitoring. This enables intelligence-led risk mitigation and incident responses, which wouldn't be possible without an automatic system.
For more information on how Darkbeam can support your business in measuring and mitigating third-party cyber risks as well as continuous dark web monitoring for early detection of real-world threats, please contact us using the form below or call +44 (0)20 3833 0348.
