Supply-Chain series: Part 2 of 4
With the Solarwinds attack still causing ripples across cybersecurity news environment, and after defining a supply chain attack, we thought it might be useful to curate some useful examples and information on supply chain attacks into a single place. After all, with so much information available to the cybersecurity sector, sometimes the real skill is in filtering out the irrelevance.
Types of supply chain attacks
With supply chain attacks often being complex, multi-organizational affairs, understanding a basic summary of the different types is important. The National Cyber Security Centre has a good overview, pointing to the four main types it sees:
- Third-party software producers: Malicious code being embedded in software that you deploy in trusted environments inside your organisation.
- Website builders: Infiltrating the processes used by creative and digital agencies to insert malicious redirects into legitimate websites.
- Third-party data stores: Organisations often outsource the collection and analysis of their data to larger aggregators. This makes them a ripe target for attackers, as obviously lots of valuable information collects in a single place.
- Watering hole attacks: An attacker identifies the places where users of a target organisation frequent, specific news sites and portals for example, and compromises these, waiting for victims.
What do the major frameworks say?
Supply Chain compromise is listed as an initial access technique in MITRE ATT&CK – with the organisation highlighting 9 stages in the supply chain they see as being vulnerable. MITRE sees the largest threat coming from vulnerabilities, with the main proposed mitigations being vulnerability scanning, patch management and detection by testing software and hardware.
NIST updated their framework in April 2018 to include supply-chain risk as well as authoring a draft publication on March 2020 with useful guidance on the topic. This included a number of best-practice case studies for how well-known organisations such as Intel and Boeing are approaching supply-chain risk.
Examples of supply chain attacks
Solarwinds
Type: Software compromise
Impacted: Government organizations and Fortune 500 companies globally
Description: An excellent example of a ‘low and slow’ supply chain attack which abuses the trust target organisations have in their software suppliers. As a Network Management System, this meant Solarwinds had more access than most - sitting at the heart of an environment. Once infected by a suspected Russian nation-state group, organizations would be subjected to a stealthy ‘hands on keyboard’ infiltration that was very hard to detect.
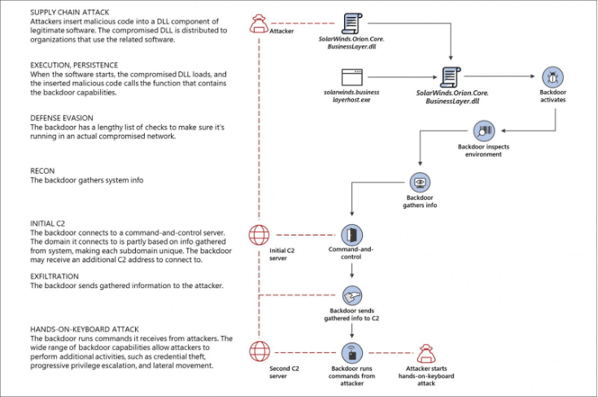
Source: Microsoft
Shylock malware
Type: Website compromise
Impacted: At least 30,000 users
Description: Targeted financial info by keylogging details of transactions taking place on websites it had embedded itself on by poisoning the web development cycle at digital agencies. The control infrastructure was taken down by a joint law enforcement action shortly afterwards.
Target
Type: Credentials theft from third-party supplier
Impacted: 40 m customer details breached, share price fall of 46%
Description: Sources allege that attackers stole network login credentials from a third-party firm monitoring the cooling systems inside the retailer, before moving sideways to more sensitive systems.
NotPetya
Type: Software compromise
Impacted: The entire country of Ukraine – ministries, banks, transport infrastructure, companies
Description: Security experts believe updates in an innocuous Ukrainian tax accounting package, called MeDoc, were compromised to deliver ransomware. This crippled infected systems and ultimately led to everything from blackouts, to a failure of radiation monitoring at Chernobyl.
What can I do about Supply Chain attacks?
Trust is crucial in business; however attackers abuse this as an enabling factor for attack vectors. Large organisations innately trust the smaller companies who supply them. With this trust, comes the access and privileges which threat actors need to make a real impact.
Mitigation is a two-way thing. Suppliers must practice good cyber security hygiene and frequently vet technical environments and educate staff around the importance of good cybersecurity practices.
For large organisations, visibility is crucial. Understanding the cyber risk presented by their suppliers is crucial. This means collecting regular digital risk intelligence on the smaller companies they work with. While this hasn’t always been easy, there are now platforms for collecting the public domain threat intelligence on suppliers that don’t require human analysis or expensive consultancy. Done regularly enough, this can form a baseline understanding of third-party risk.
